mirror of https://github.com/go-gitea/gitea
Add RPM registry (#23380)
Fixes #20751 This PR adds a RPM package registry. You can follow [this tutorial](https://opensource.com/article/18/9/how-build-rpm-packages) to build a *.rpm package for testing. This functionality is similar to the Debian registry (#22854) and therefore shares some methods. I marked this PR as blocked because it should be merged after #22854. 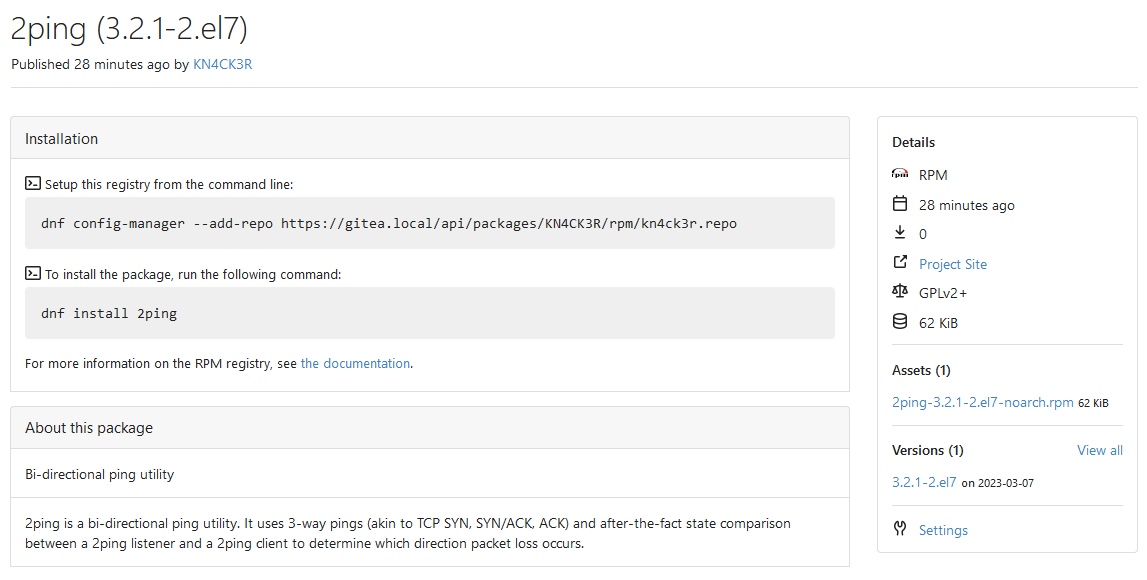pull/24554/head
parent
8f314c6793
commit
05209f0d1d
File diff suppressed because one or more lines are too long
@ -0,0 +1,118 @@ |
||||
--- |
||||
date: "2023-03-08T00:00:00+00:00" |
||||
title: "RPM Packages Repository" |
||||
slug: "packages/rpm" |
||||
draft: false |
||||
toc: false |
||||
menu: |
||||
sidebar: |
||||
parent: "packages" |
||||
name: "RPM" |
||||
weight: 105 |
||||
identifier: "rpm" |
||||
--- |
||||
|
||||
# RPM Packages Repository |
||||
|
||||
Publish [RPM](https://rpm.org/) packages for your user or organization. |
||||
|
||||
**Table of Contents** |
||||
|
||||
{{< toc >}} |
||||
|
||||
## Requirements |
||||
|
||||
To work with the RPM registry, you need to use a package manager like `yum` or `dnf` to consume packages. |
||||
|
||||
The following examples use `dnf`. |
||||
|
||||
## Configuring the package registry |
||||
|
||||
To register the RPM registry add the url to the list of known apt sources: |
||||
|
||||
```shell |
||||
dnf config-manager --add-repo https://gitea.example.com/api/packages/{owner}/rpm.repo |
||||
``` |
||||
|
||||
| Placeholder | Description | |
||||
| ----------- | ----------- | |
||||
| `owner` | The owner of the package. | |
||||
|
||||
If the registry is private, provide credentials in the url. You can use a password or a [personal access token]({{< relref "doc/developers/api-usage.en-us.md#authentication" >}}): |
||||
|
||||
```shell |
||||
dnf config-manager --add-repo https://{username}:{your_password_or_token}@gitea.example.com/api/packages/{owner}/rpm.repo |
||||
``` |
||||
|
||||
You have to add the credentials to the urls in the `rpm.repo` file in `/etc/yum.repos.d` too. |
||||
|
||||
## Publish a package |
||||
|
||||
To publish a RPM package (`*.rpm`), perform a HTTP PUT operation with the package content in the request body. |
||||
|
||||
``` |
||||
PUT https://gitea.example.com/api/packages/{owner}/rpm/upload |
||||
``` |
||||
|
||||
| Parameter | Description | |
||||
| --------- | ----------- | |
||||
| `owner` | The owner of the package. | |
||||
|
||||
Example request using HTTP Basic authentication: |
||||
|
||||
```shell |
||||
curl --user your_username:your_password_or_token \ |
||||
--upload-file path/to/file.rpm \ |
||||
https://gitea.example.com/api/packages/testuser/rpm/upload |
||||
``` |
||||
|
||||
If you are using 2FA or OAuth use a [personal access token]({{< relref "doc/developers/api-usage.en-us.md#authentication" >}}) instead of the password. |
||||
You cannot publish a file with the same name twice to a package. You must delete the existing package version first. |
||||
|
||||
The server reponds with the following HTTP Status codes. |
||||
|
||||
| HTTP Status Code | Meaning | |
||||
| ----------------- | ------- | |
||||
| `201 Created` | The package has been published. | |
||||
| `400 Bad Request` | The package is invalid. | |
||||
| `409 Conflict` | A package file with the same combination of parameters exist already in the package. | |
||||
|
||||
## Delete a package |
||||
|
||||
To delete a Debian package perform a HTTP DELETE operation. This will delete the package version too if there is no file left. |
||||
|
||||
``` |
||||
DELETE https://gitea.example.com/api/packages/{owner}/rpm/{package_name}/{package_version}/{architecture} |
||||
``` |
||||
|
||||
| Parameter | Description | |
||||
| ----------------- | ----------- | |
||||
| `owner` | The owner of the package. | |
||||
| `package_name` | The package name. | |
||||
| `package_version` | The package version. | |
||||
| `architecture` | The package architecture. | |
||||
|
||||
Example request using HTTP Basic authentication: |
||||
|
||||
```shell |
||||
curl --user your_username:your_token_or_password -X DELETE \ |
||||
https://gitea.example.com/api/packages/testuser/rpm/test-package/1.0.0/x86_64 |
||||
``` |
||||
|
||||
The server reponds with the following HTTP Status codes. |
||||
|
||||
| HTTP Status Code | Meaning | |
||||
| ----------------- | ------- | |
||||
| `204 No Content` | Success | |
||||
| `404 Not Found` | The package or file was not found. | |
||||
|
||||
## Install a package |
||||
|
||||
To install a package from the RPM registry, execute the following commands: |
||||
|
||||
```shell |
||||
# use latest version |
||||
dnf install {package_name} |
||||
# use specific version |
||||
dnf install {package_name}-{package_version}.{architecture} |
||||
``` |
||||
@ -0,0 +1,296 @@ |
||||
// Copyright 2023 The Gitea Authors. All rights reserved.
|
||||
// SPDX-License-Identifier: MIT
|
||||
|
||||
package rpm |
||||
|
||||
import ( |
||||
"fmt" |
||||
"io" |
||||
"strings" |
||||
|
||||
"code.gitea.io/gitea/modules/timeutil" |
||||
"code.gitea.io/gitea/modules/validation" |
||||
|
||||
"github.com/sassoftware/go-rpmutils" |
||||
) |
||||
|
||||
const ( |
||||
PropertyMetadata = "rpm.metdata" |
||||
|
||||
SettingKeyPrivate = "rpm.key.private" |
||||
SettingKeyPublic = "rpm.key.public" |
||||
|
||||
RepositoryPackage = "_rpm" |
||||
RepositoryVersion = "_repository" |
||||
) |
||||
|
||||
const ( |
||||
// Can't use the syscall constants because they are not available for windows build.
|
||||
sIFMT = 0xf000 |
||||
sIFDIR = 0x4000 |
||||
sIXUSR = 0x40 |
||||
sIXGRP = 0x8 |
||||
sIXOTH = 0x1 |
||||
) |
||||
|
||||
// https://rpm-software-management.github.io/rpm/manual/spec.html
|
||||
// https://refspecs.linuxbase.org/LSB_3.1.0/LSB-Core-generic/LSB-Core-generic/pkgformat.html
|
||||
|
||||
type Package struct { |
||||
Name string |
||||
Version string |
||||
VersionMetadata *VersionMetadata |
||||
FileMetadata *FileMetadata |
||||
} |
||||
|
||||
type VersionMetadata struct { |
||||
License string `json:"license,omitempty"` |
||||
ProjectURL string `json:"project_url,omitempty"` |
||||
Summary string `json:"summary,omitempty"` |
||||
Description string `json:"description,omitempty"` |
||||
} |
||||
|
||||
type FileMetadata struct { |
||||
Architecture string `json:"architecture,omitempty"` |
||||
Epoch string `json:"epoch,omitempty"` |
||||
Version string `json:"version,omitempty"` |
||||
Release string `json:"release,omitempty"` |
||||
Vendor string `json:"vendor,omitempty"` |
||||
Group string `json:"group,omitempty"` |
||||
Packager string `json:"packager,omitempty"` |
||||
SourceRpm string `json:"source_rpm,omitempty"` |
||||
BuildHost string `json:"build_host,omitempty"` |
||||
BuildTime uint64 `json:"build_time,omitempty"` |
||||
FileTime uint64 `json:"file_time,omitempty"` |
||||
InstalledSize uint64 `json:"installed_size,omitempty"` |
||||
ArchiveSize uint64 `json:"archive_size,omitempty"` |
||||
|
||||
Provides []*Entry `json:"provide,omitempty"` |
||||
Requires []*Entry `json:"require,omitempty"` |
||||
Conflicts []*Entry `json:"conflict,omitempty"` |
||||
Obsoletes []*Entry `json:"obsolete,omitempty"` |
||||
|
||||
Files []*File `json:"files,omitempty"` |
||||
|
||||
Changelogs []*Changelog `json:"changelogs,omitempty"` |
||||
} |
||||
|
||||
type Entry struct { |
||||
Name string `json:"name" xml:"name,attr"` |
||||
Flags string `json:"flags,omitempty" xml:"flags,attr,omitempty"` |
||||
Version string `json:"version,omitempty" xml:"ver,attr,omitempty"` |
||||
Epoch string `json:"epoch,omitempty" xml:"epoch,attr,omitempty"` |
||||
Release string `json:"release,omitempty" xml:"rel,attr,omitempty"` |
||||
} |
||||
|
||||
type File struct { |
||||
Path string `json:"path" xml:",chardata"` |
||||
Type string `json:"type,omitempty" xml:"type,attr,omitempty"` |
||||
IsExecutable bool `json:"is_executable" xml:"-"` |
||||
} |
||||
|
||||
type Changelog struct { |
||||
Author string `json:"author,omitempty" xml:"author,attr"` |
||||
Date timeutil.TimeStamp `json:"date,omitempty" xml:"date,attr"` |
||||
Text string `json:"text,omitempty" xml:",chardata"` |
||||
} |
||||
|
||||
// ParsePackage parses the RPM package file
|
||||
func ParsePackage(r io.Reader) (*Package, error) { |
||||
rpm, err := rpmutils.ReadRpm(r) |
||||
if err != nil { |
||||
return nil, err |
||||
} |
||||
|
||||
nevra, err := rpm.Header.GetNEVRA() |
||||
if err != nil { |
||||
return nil, err |
||||
} |
||||
|
||||
version := fmt.Sprintf("%s-%s", nevra.Version, nevra.Release) |
||||
if nevra.Epoch != "" && nevra.Epoch != "0" { |
||||
version = fmt.Sprintf("%s-%s", nevra.Epoch, version) |
||||
} |
||||
|
||||
p := &Package{ |
||||
Name: nevra.Name, |
||||
Version: version, |
||||
VersionMetadata: &VersionMetadata{ |
||||
Summary: getString(rpm.Header, rpmutils.SUMMARY), |
||||
Description: getString(rpm.Header, rpmutils.DESCRIPTION), |
||||
License: getString(rpm.Header, rpmutils.LICENSE), |
||||
ProjectURL: getString(rpm.Header, rpmutils.URL), |
||||
}, |
||||
FileMetadata: &FileMetadata{ |
||||
Architecture: nevra.Arch, |
||||
Epoch: nevra.Epoch, |
||||
Version: nevra.Version, |
||||
Release: nevra.Release, |
||||
Vendor: getString(rpm.Header, rpmutils.VENDOR), |
||||
Group: getString(rpm.Header, rpmutils.GROUP), |
||||
Packager: getString(rpm.Header, rpmutils.PACKAGER), |
||||
SourceRpm: getString(rpm.Header, rpmutils.SOURCERPM), |
||||
BuildHost: getString(rpm.Header, rpmutils.BUILDHOST), |
||||
BuildTime: getUInt64(rpm.Header, rpmutils.BUILDTIME), |
||||
FileTime: getUInt64(rpm.Header, rpmutils.FILEMTIMES), |
||||
InstalledSize: getUInt64(rpm.Header, rpmutils.SIZE), |
||||
ArchiveSize: getUInt64(rpm.Header, rpmutils.SIG_PAYLOADSIZE), |
||||
|
||||
Provides: getEntries(rpm.Header, rpmutils.PROVIDENAME, rpmutils.PROVIDEVERSION, rpmutils.PROVIDEFLAGS), |
||||
Requires: getEntries(rpm.Header, rpmutils.REQUIRENAME, rpmutils.REQUIREVERSION, rpmutils.REQUIREFLAGS), |
||||
Conflicts: getEntries(rpm.Header, 1054 /*rpmutils.CONFLICTNAME*/, 1055 /*rpmutils.CONFLICTVERSION*/, 1053 /*rpmutils.CONFLICTFLAGS*/), // https://github.com/sassoftware/go-rpmutils/pull/24
|
||||
Obsoletes: getEntries(rpm.Header, rpmutils.OBSOLETENAME, rpmutils.OBSOLETEVERSION, rpmutils.OBSOLETEFLAGS), |
||||
Files: getFiles(rpm.Header), |
||||
Changelogs: getChangelogs(rpm.Header), |
||||
}, |
||||
} |
||||
|
||||
if !validation.IsValidURL(p.VersionMetadata.ProjectURL) { |
||||
p.VersionMetadata.ProjectURL = "" |
||||
} |
||||
|
||||
return p, nil |
||||
} |
||||
|
||||
func getString(h *rpmutils.RpmHeader, tag int) string { |
||||
values, err := h.GetStrings(tag) |
||||
if err != nil || len(values) < 1 { |
||||
return "" |
||||
} |
||||
return values[0] |
||||
} |
||||
|
||||
func getUInt64(h *rpmutils.RpmHeader, tag int) uint64 { |
||||
values, err := h.GetUint64s(tag) |
||||
if err != nil || len(values) < 1 { |
||||
return 0 |
||||
} |
||||
return values[0] |
||||
} |
||||
|
||||
func getEntries(h *rpmutils.RpmHeader, namesTag, versionsTag, flagsTag int) []*Entry { |
||||
names, err := h.GetStrings(namesTag) |
||||
if err != nil || len(names) == 0 { |
||||
return nil |
||||
} |
||||
flags, err := h.GetUint64s(flagsTag) |
||||
if err != nil || len(flags) == 0 { |
||||
return nil |
||||
} |
||||
versions, err := h.GetStrings(versionsTag) |
||||
if err != nil || len(versions) == 0 { |
||||
return nil |
||||
} |
||||
if len(names) != len(flags) || len(names) != len(versions) { |
||||
return nil |
||||
} |
||||
|
||||
entries := make([]*Entry, 0, len(names)) |
||||
for i := range names { |
||||
e := &Entry{ |
||||
Name: names[i], |
||||
} |
||||
|
||||
flags := flags[i] |
||||
if (flags&rpmutils.RPMSENSE_GREATER) != 0 && (flags&rpmutils.RPMSENSE_EQUAL) != 0 { |
||||
e.Flags = "GE" |
||||
} else if (flags&rpmutils.RPMSENSE_LESS) != 0 && (flags&rpmutils.RPMSENSE_EQUAL) != 0 { |
||||
e.Flags = "LE" |
||||
} else if (flags & rpmutils.RPMSENSE_GREATER) != 0 { |
||||
e.Flags = "GT" |
||||
} else if (flags & rpmutils.RPMSENSE_LESS) != 0 { |
||||
e.Flags = "LT" |
||||
} else if (flags & rpmutils.RPMSENSE_EQUAL) != 0 { |
||||
e.Flags = "EQ" |
||||
} |
||||
|
||||
version := versions[i] |
||||
if version != "" { |
||||
parts := strings.Split(version, "-") |
||||
|
||||
versionParts := strings.Split(parts[0], ":") |
||||
if len(versionParts) == 2 { |
||||
e.Version = versionParts[1] |
||||
e.Epoch = versionParts[0] |
||||
} else { |
||||
e.Version = versionParts[0] |
||||
e.Epoch = "0" |
||||
} |
||||
|
||||
if len(parts) > 1 { |
||||
e.Release = parts[1] |
||||
} |
||||
} |
||||
|
||||
entries = append(entries, e) |
||||
} |
||||
return entries |
||||
} |
||||
|
||||
func getFiles(h *rpmutils.RpmHeader) []*File { |
||||
baseNames, _ := h.GetStrings(rpmutils.BASENAMES) |
||||
dirNames, _ := h.GetStrings(rpmutils.DIRNAMES) |
||||
dirIndexes, _ := h.GetUint32s(rpmutils.DIRINDEXES) |
||||
fileFlags, _ := h.GetUint32s(rpmutils.FILEFLAGS) |
||||
fileModes, _ := h.GetUint32s(rpmutils.FILEMODES) |
||||
|
||||
files := make([]*File, 0, len(baseNames)) |
||||
for i := range baseNames { |
||||
if len(dirIndexes) <= i { |
||||
continue |
||||
} |
||||
dirIndex := dirIndexes[i] |
||||
if len(dirNames) <= int(dirIndex) { |
||||
continue |
||||
} |
||||
|
||||
var fileType string |
||||
var isExecutable bool |
||||
if i < len(fileFlags) && (fileFlags[i]&rpmutils.RPMFILE_GHOST) != 0 { |
||||
fileType = "ghost" |
||||
} else if i < len(fileModes) { |
||||
if (fileModes[i] & sIFMT) == sIFDIR { |
||||
fileType = "dir" |
||||
} else { |
||||
mode := fileModes[i] & ^uint32(sIFMT) |
||||
isExecutable = (mode&sIXUSR) != 0 || (mode&sIXGRP) != 0 || (mode&sIXOTH) != 0 |
||||
} |
||||
} |
||||
|
||||
files = append(files, &File{ |
||||
Path: dirNames[dirIndex] + baseNames[i], |
||||
Type: fileType, |
||||
IsExecutable: isExecutable, |
||||
}) |
||||
} |
||||
|
||||
return files |
||||
} |
||||
|
||||
func getChangelogs(h *rpmutils.RpmHeader) []*Changelog { |
||||
texts, err := h.GetStrings(rpmutils.CHANGELOGTEXT) |
||||
if err != nil || len(texts) == 0 { |
||||
return nil |
||||
} |
||||
authors, err := h.GetStrings(rpmutils.CHANGELOGNAME) |
||||
if err != nil || len(authors) == 0 { |
||||
return nil |
||||
} |
||||
times, err := h.GetUint32s(rpmutils.CHANGELOGTIME) |
||||
if err != nil || len(times) == 0 { |
||||
return nil |
||||
} |
||||
if len(texts) != len(authors) || len(texts) != len(times) { |
||||
return nil |
||||
} |
||||
|
||||
changelogs := make([]*Changelog, 0, len(texts)) |
||||
for i := range texts { |
||||
changelogs = append(changelogs, &Changelog{ |
||||
Author: authors[i], |
||||
Date: timeutil.TimeStamp(times[i]), |
||||
Text: texts[i], |
||||
}) |
||||
} |
||||
return changelogs |
||||
} |
||||
@ -0,0 +1,163 @@ |
||||
// Copyright 2023 The Gitea Authors. All rights reserved.
|
||||
// SPDX-License-Identifier: MIT
|
||||
|
||||
package rpm |
||||
|
||||
import ( |
||||
"bytes" |
||||
"compress/gzip" |
||||
"encoding/base64" |
||||
"testing" |
||||
|
||||
"github.com/stretchr/testify/assert" |
||||
) |
||||
|
||||
func TestParsePackage(t *testing.T) { |
||||
base64RpmPackageContent := `H4sICFayB2QCAGdpdGVhLXRlc3QtMS4wLjItMS14ODZfNjQucnBtAO2YV4gTQRjHJzl7wbNhhxVF |
||||
VNwk2zd2PdvZ9Sxnd3Z3NllNsmF3o6congVFsWFHRWwIImIXfRER0QcRfPBJEXvvBQvWSfZTT0VQ |
||||
8TF/MuU33zcz3+zOJGEe73lyuQBRBWKWRzDrEddjuVAkxLMc+lsFUOWfm5bvvReAalWECg/TsivU |
||||
dyKa0U61aVnl6wj0Uxe4nc8F92hZiaYE8CO/P0r7/Quegr0c7M/AvoCaGZEIWNGUqMHrhhGROIUT |
||||
Zc7gOAOraoQzCNZ0WdU0HpEI5jiB4zlek3gT85wqCBomhomxoGCs8wImWMImbxqKgXVNUKKaqShR |
||||
STKVKK9glFUNcf2g+/t27xs16v5x/eyOKftVGlIhyiuvvPLKK6+88sorr7zyyiuvvPKCO5HPnz+v |
||||
pGVhhXsTsFVeSstuWR9anwU+Bk3Vch5wTwL3JkHg+8C1gR8A169wj1KdpobAj4HbAT+Be5VewE+h |
||||
fz/g52AvBX4N9vHAb4AnA7+F8ePAH8BuA38ELgf+BLzQ50oIeBlw0OdAOXAlP57AGuCsbwGtbgCu |
||||
DrwRuAb4bwau6T/PwFbgWsDXgWuD/y3gOmC/B1wI/Bi4AcT3Arih3z9YCNzI9w9m/YKUG4Nd9N9z |
||||
pSZgHwrcFPgccFt//OADGE+F/q+Ao+D/FrijzwV1gbv4/QvaAHcFDgF3B5aB+wB3Be7rz1dQCtwP
|
||||
eDxwMcw3GbgU7AasdwzYE8DjwT4L/CeAvRx4IvBCYA3iWQds+FzpDjABfghsAj8BTgA/A/b8+StX |
||||
A84A1wKe5s9fuRB4JpzHZv55rL8a/Dv49vpn/PErR4BvQX8Z+Db4l2W5CH2/f0W5+1fEoeFDBzFp |
||||
rE/FMcK4mWQSOzN+aDOIqztW2rPsFKIyqh7sQERR42RVMSKihnzVHlQ8Ag0YLBYNEIajkhmuR5Io |
||||
7nlpt2M4nJs0ZNkoYaUyZahMlSfJImr1n1WjFVNCPCaTZgYNGdGL8YN2mX8WHfA/C7ViHJK0pxHG |
||||
SrkeTiSI4T+7ubf85yrzRCQRQ5EVxVAjvIBVRY/KRFAVReIkhfARSddNSceayQkGliIKb0q8RAxJ |
||||
5QWNVxHIsW3Pz369bw+5jh5y0klE9Znqm0dF57b0HbGy2A5lVUBTZZrqZjdUjYoprFmpsBtHP5d0 |
||||
+ISltS2yk2mHuC4x+lgJMhgnidvuqy3b0suK0bm+tw3FMxI2zjm7/fA0MtQhplX2s7nYLZ2ZC0yg |
||||
CxJZDokhORTJlrlcCvG5OieGBERlVCs7CfuS6WzQ/T2j+9f92BWxTFEcp2IkYccYGp2LYySEfreq |
||||
irue4WRF5XkpKovw2wgpq2rZBI8bQZkzxEkiYaNwxnXCCVvHidzIiB3CM2yMYdNWmjDsaLovaE4c |
||||
x3a6mLaTxB7rEj3jWN4M2p7uwPaa1GfI8BHFfcZMKhkycnhR7y781/a+A4t7FpWWTupRUtKbegwZ |
||||
XMKwJinTSe70uhRcj55qNu3YHtE922Fdz7FTMTq9Q3TbMdiYrrPudMvT44S6u2miu138eC0tTN9D |
||||
2CFGHHtQsHHsGCRFDFbXuT9wx6mUTZfseydlkWZeJkW6xOgYjqXT+LA7I6XHaUx2xmUzqelWymA9 |
||||
rCXI9+D1BHbjsITssqhBNysw0tOWjcpmIh6+aViYPfftw8ZSGfRVPUqKiosZj5R5qGmk/8AjjRbZ |
||||
d8b3vvngdPHx3HvMeCarIk7VVSwbgoZVkceEVyOmyUmGxBGNYDVKSFSOGlIkGqWnUZFkiY/wsmhK |
||||
Mu0UFYgZ/bYnuvn/vz4wtCz8qMwsHUvP0PX3tbYFUctAPdrY6tiiDtcCddDECahx7SuVNP5dpmb5 |
||||
9tMDyaXb7OAlk5acuPn57ss9mw6Wym0m1Fq2cej7tUt2LL4/b8enXU2fndk+fvv57ndnt55/cQob |
||||
7tpp/pEjDS7cGPZ6BY430+7danDq6f42Nw49b9F7zp6BiKpJb9s5P0AYN2+L159cnrur636rx+v1 |
||||
7ae1K28QbMMcqI8CqwIrgwg9nTOp8Oj9q81plUY7ZuwXN8Vvs8wbAAA=` |
||||
rpmPackageContent, err := base64.StdEncoding.DecodeString(base64RpmPackageContent) |
||||
assert.NoError(t, err) |
||||
|
||||
zr, err := gzip.NewReader(bytes.NewReader(rpmPackageContent)) |
||||
assert.NoError(t, err) |
||||
|
||||
p, err := ParsePackage(zr) |
||||
assert.NotNil(t, p) |
||||
assert.NoError(t, err) |
||||
|
||||
assert.Equal(t, "gitea-test", p.Name) |
||||
assert.Equal(t, "1.0.2-1", p.Version) |
||||
assert.NotNil(t, p.VersionMetadata) |
||||
assert.NotNil(t, p.FileMetadata) |
||||
|
||||
assert.Equal(t, "MIT", p.VersionMetadata.License) |
||||
assert.Equal(t, "https://gitea.io", p.VersionMetadata.ProjectURL) |
||||
assert.Equal(t, "RPM package summary", p.VersionMetadata.Summary) |
||||
assert.Equal(t, "RPM package description", p.VersionMetadata.Description) |
||||
|
||||
assert.Equal(t, "x86_64", p.FileMetadata.Architecture) |
||||
assert.Equal(t, "0", p.FileMetadata.Epoch) |
||||
assert.Equal(t, "1.0.2", p.FileMetadata.Version) |
||||
assert.Equal(t, "1", p.FileMetadata.Release) |
||||
assert.Empty(t, p.FileMetadata.Vendor) |
||||
assert.Equal(t, "KN4CK3R", p.FileMetadata.Packager) |
||||
assert.Equal(t, "gitea-test-1.0.2-1.src.rpm", p.FileMetadata.SourceRpm) |
||||
assert.Equal(t, "e44b1687d04b", p.FileMetadata.BuildHost) |
||||
assert.EqualValues(t, 1678225964, p.FileMetadata.BuildTime) |
||||
assert.EqualValues(t, 1678225964, p.FileMetadata.FileTime) |
||||
assert.EqualValues(t, 13, p.FileMetadata.InstalledSize) |
||||
assert.EqualValues(t, 272, p.FileMetadata.ArchiveSize) |
||||
assert.Empty(t, p.FileMetadata.Conflicts) |
||||
assert.Empty(t, p.FileMetadata.Obsoletes) |
||||
|
||||
assert.ElementsMatch( |
||||
t, |
||||
[]*Entry{ |
||||
{ |
||||
Name: "gitea-test", |
||||
Flags: "EQ", |
||||
Version: "1.0.2", |
||||
Epoch: "0", |
||||
Release: "1", |
||||
}, |
||||
{ |
||||
Name: "gitea-test(x86-64)", |
||||
Flags: "EQ", |
||||
Version: "1.0.2", |
||||
Epoch: "0", |
||||
Release: "1", |
||||
}, |
||||
}, |
||||
p.FileMetadata.Provides, |
||||
) |
||||
assert.ElementsMatch( |
||||
t, |
||||
[]*Entry{ |
||||
{ |
||||
Name: "/bin/sh", |
||||
}, |
||||
{ |
||||
Name: "/bin/sh", |
||||
}, |
||||
{ |
||||
Name: "/bin/sh", |
||||
}, |
||||
{ |
||||
Name: "rpmlib(CompressedFileNames)", |
||||
Flags: "LE", |
||||
Version: "3.0.4", |
||||
Epoch: "0", |
||||
Release: "1", |
||||
}, |
||||
{ |
||||
Name: "rpmlib(FileDigests)", |
||||
Flags: "LE", |
||||
Version: "4.6.0", |
||||
Epoch: "0", |
||||
Release: "1", |
||||
}, |
||||
{ |
||||
Name: "rpmlib(PayloadFilesHavePrefix)", |
||||
Flags: "LE", |
||||
Version: "4.0", |
||||
Epoch: "0", |
||||
Release: "1", |
||||
}, |
||||
{ |
||||
Name: "rpmlib(PayloadIsXz)", |
||||
Flags: "LE", |
||||
Version: "5.2", |
||||
Epoch: "0", |
||||
Release: "1", |
||||
}, |
||||
}, |
||||
p.FileMetadata.Requires, |
||||
) |
||||
assert.ElementsMatch( |
||||
t, |
||||
[]*File{ |
||||
{ |
||||
Path: "/usr/local/bin/hello", |
||||
IsExecutable: true, |
||||
}, |
||||
}, |
||||
p.FileMetadata.Files, |
||||
) |
||||
assert.ElementsMatch( |
||||
t, |
||||
[]*Changelog{ |
||||
{ |
||||
Author: "KN4CK3R <dummy@gitea.io>", |
||||
Date: 1678276800, |
||||
Text: "- Changelog message.", |
||||
}, |
||||
}, |
||||
p.FileMetadata.Changelogs, |
||||
) |
||||
} |
||||
|
After Width: | Height: | Size: 2.6 KiB |
@ -0,0 +1,268 @@ |
||||
// Copyright 2023 The Gitea Authors. All rights reserved.
|
||||
// SPDX-License-Identifier: MIT
|
||||
|
||||
package rpm |
||||
|
||||
import ( |
||||
stdctx "context" |
||||
"errors" |
||||
"fmt" |
||||
"io" |
||||
"net/http" |
||||
"strings" |
||||
|
||||
"code.gitea.io/gitea/models/db" |
||||
packages_model "code.gitea.io/gitea/models/packages" |
||||
"code.gitea.io/gitea/modules/context" |
||||
"code.gitea.io/gitea/modules/json" |
||||
"code.gitea.io/gitea/modules/notification" |
||||
packages_module "code.gitea.io/gitea/modules/packages" |
||||
rpm_module "code.gitea.io/gitea/modules/packages/rpm" |
||||
"code.gitea.io/gitea/modules/setting" |
||||
"code.gitea.io/gitea/modules/util" |
||||
"code.gitea.io/gitea/routers/api/packages/helper" |
||||
packages_service "code.gitea.io/gitea/services/packages" |
||||
rpm_service "code.gitea.io/gitea/services/packages/rpm" |
||||
) |
||||
|
||||
func apiError(ctx *context.Context, status int, obj interface{}) { |
||||
helper.LogAndProcessError(ctx, status, obj, func(message string) { |
||||
ctx.PlainText(status, message) |
||||
}) |
||||
} |
||||
|
||||
// https://dnf.readthedocs.io/en/latest/conf_ref.html
|
||||
func GetRepositoryConfig(ctx *context.Context) { |
||||
url := fmt.Sprintf("%sapi/packages/%s/rpm", setting.AppURL, ctx.Package.Owner.Name) |
||||
|
||||
ctx.PlainText(http.StatusOK, `[gitea-`+ctx.Package.Owner.LowerName+`] |
||||
name=`+ctx.Package.Owner.Name+` - `+setting.AppName+` |
||||
baseurl=`+url+` |
||||
enabled=1 |
||||
gpgcheck=1 |
||||
gpgkey=`+url+`/repository.key`) |
||||
} |
||||
|
||||
// Gets or creates the PGP public key used to sign repository metadata files
|
||||
func GetRepositoryKey(ctx *context.Context) { |
||||
_, pub, err := rpm_service.GetOrCreateKeyPair(ctx.Package.Owner.ID) |
||||
if err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
|
||||
ctx.ServeContent(strings.NewReader(pub), &context.ServeHeaderOptions{ |
||||
ContentType: "application/pgp-keys", |
||||
Filename: "repository.key", |
||||
}) |
||||
} |
||||
|
||||
// Gets a pre-generated repository metadata file
|
||||
func GetRepositoryFile(ctx *context.Context) { |
||||
pv, err := rpm_service.GetOrCreateRepositoryVersion(ctx.Package.Owner.ID) |
||||
if err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
|
||||
s, pf, err := packages_service.GetFileStreamByPackageVersion( |
||||
ctx, |
||||
pv, |
||||
&packages_service.PackageFileInfo{ |
||||
Filename: ctx.Params("filename"), |
||||
}, |
||||
) |
||||
if err != nil { |
||||
if errors.Is(err, util.ErrNotExist) { |
||||
apiError(ctx, http.StatusNotFound, err) |
||||
} else { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
} |
||||
return |
||||
} |
||||
defer s.Close() |
||||
|
||||
ctx.ServeContent(s, &context.ServeHeaderOptions{ |
||||
Filename: pf.Name, |
||||
LastModified: pf.CreatedUnix.AsLocalTime(), |
||||
}) |
||||
} |
||||
|
||||
func UploadPackageFile(ctx *context.Context) { |
||||
upload, close, err := ctx.UploadStream() |
||||
if err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
if close { |
||||
defer upload.Close() |
||||
} |
||||
|
||||
buf, err := packages_module.CreateHashedBufferFromReader(upload) |
||||
if err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
defer buf.Close() |
||||
|
||||
pck, err := rpm_module.ParsePackage(buf) |
||||
if err != nil { |
||||
if errors.Is(err, util.ErrInvalidArgument) { |
||||
apiError(ctx, http.StatusBadRequest, err) |
||||
} else { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
} |
||||
return |
||||
} |
||||
|
||||
if _, err := buf.Seek(0, io.SeekStart); err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
|
||||
fileMetadataRaw, err := json.Marshal(pck.FileMetadata) |
||||
if err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
|
||||
_, _, err = packages_service.CreatePackageOrAddFileToExisting( |
||||
&packages_service.PackageCreationInfo{ |
||||
PackageInfo: packages_service.PackageInfo{ |
||||
Owner: ctx.Package.Owner, |
||||
PackageType: packages_model.TypeRpm, |
||||
Name: pck.Name, |
||||
Version: pck.Version, |
||||
}, |
||||
Creator: ctx.Doer, |
||||
Metadata: pck.VersionMetadata, |
||||
}, |
||||
&packages_service.PackageFileCreationInfo{ |
||||
PackageFileInfo: packages_service.PackageFileInfo{ |
||||
Filename: fmt.Sprintf("%s-%s.%s.rpm", pck.Name, pck.Version, pck.FileMetadata.Architecture), |
||||
}, |
||||
Creator: ctx.Doer, |
||||
Data: buf, |
||||
IsLead: true, |
||||
Properties: map[string]string{ |
||||
rpm_module.PropertyMetadata: string(fileMetadataRaw), |
||||
}, |
||||
}, |
||||
) |
||||
if err != nil { |
||||
switch err { |
||||
case packages_model.ErrDuplicatePackageVersion, packages_model.ErrDuplicatePackageFile: |
||||
apiError(ctx, http.StatusConflict, err) |
||||
case packages_service.ErrQuotaTotalCount, packages_service.ErrQuotaTypeSize, packages_service.ErrQuotaTotalSize: |
||||
apiError(ctx, http.StatusForbidden, err) |
||||
default: |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
} |
||||
return |
||||
} |
||||
|
||||
if err := rpm_service.BuildRepositoryFiles(ctx, ctx.Package.Owner.ID); err != nil { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
|
||||
ctx.Status(http.StatusCreated) |
||||
} |
||||
|
||||
func DownloadPackageFile(ctx *context.Context) { |
||||
name := ctx.Params("name") |
||||
version := ctx.Params("version") |
||||
|
||||
s, pf, err := packages_service.GetFileStreamByPackageNameAndVersion( |
||||
ctx, |
||||
&packages_service.PackageInfo{ |
||||
Owner: ctx.Package.Owner, |
||||
PackageType: packages_model.TypeRpm, |
||||
Name: name, |
||||
Version: version, |
||||
}, |
||||
&packages_service.PackageFileInfo{ |
||||
Filename: fmt.Sprintf("%s-%s.%s.rpm", name, version, ctx.Params("architecture")), |
||||
}, |
||||
) |
||||
if err != nil { |
||||
if errors.Is(err, util.ErrNotExist) { |
||||
apiError(ctx, http.StatusNotFound, err) |
||||
} else { |
||||
apiError(ctx, http.StatusInternalServerError, err) |
||||
} |
||||
return |
||||
} |
||||
defer s.Close() |
||||
|
||||
ctx.ServeContent(s, &context.ServeHeaderOptions{ |
||||
ContentType: "application/x-rpm", |
||||
Filename: pf.Name, |
||||
LastModified: pf.CreatedUnix.AsLocalTime(), |
||||
}) |
||||
} |
||||
|
||||
func DeletePackageFile(webctx *context.Context) { |
||||
name := webctx.Params("name") |
||||
version := webctx.Params("version") |
||||
architecture := webctx.Params("architecture") |
||||
|
||||
var pd *packages_model.PackageDescriptor |
||||
|
||||
err := db.WithTx(webctx, func(ctx stdctx.Context) error { |
||||
pv, err := packages_model.GetVersionByNameAndVersion(ctx, webctx.Package.Owner.ID, packages_model.TypeRpm, name, version) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
pf, err := packages_model.GetFileForVersionByName( |
||||
ctx, |
||||
pv.ID, |
||||
fmt.Sprintf("%s-%s.%s.rpm", name, version, architecture), |
||||
packages_model.EmptyFileKey, |
||||
) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
if err := packages_service.DeletePackageFile(ctx, pf); err != nil { |
||||
return err |
||||
} |
||||
|
||||
has, err := packages_model.HasVersionFileReferences(ctx, pv.ID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
if !has { |
||||
pd, err = packages_model.GetPackageDescriptor(ctx, pv) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
if err := packages_service.DeletePackageVersionAndReferences(ctx, pv); err != nil { |
||||
return err |
||||
} |
||||
} |
||||
|
||||
return nil |
||||
}) |
||||
if err != nil { |
||||
if errors.Is(err, util.ErrNotExist) { |
||||
apiError(webctx, http.StatusNotFound, err) |
||||
} else { |
||||
apiError(webctx, http.StatusInternalServerError, err) |
||||
} |
||||
return |
||||
} |
||||
|
||||
if pd != nil { |
||||
notification.NotifyPackageDelete(webctx, webctx.Doer, pd) |
||||
} |
||||
|
||||
if err := rpm_service.BuildRepositoryFiles(webctx, webctx.Package.Owner.ID); err != nil { |
||||
apiError(webctx, http.StatusInternalServerError, err) |
||||
return |
||||
} |
||||
|
||||
webctx.Status(http.StatusNoContent) |
||||
} |
||||
@ -0,0 +1,601 @@ |
||||
// Copyright 2023 The Gitea Authors. All rights reserved.
|
||||
// SPDX-License-Identifier: MIT
|
||||
|
||||
package rpm |
||||
|
||||
import ( |
||||
"bytes" |
||||
"compress/gzip" |
||||
"context" |
||||
"crypto/sha256" |
||||
"encoding/hex" |
||||
"encoding/xml" |
||||
"errors" |
||||
"fmt" |
||||
"io" |
||||
"net/url" |
||||
"strings" |
||||
"time" |
||||
|
||||
packages_model "code.gitea.io/gitea/models/packages" |
||||
user_model "code.gitea.io/gitea/models/user" |
||||
"code.gitea.io/gitea/modules/json" |
||||
packages_module "code.gitea.io/gitea/modules/packages" |
||||
rpm_module "code.gitea.io/gitea/modules/packages/rpm" |
||||
"code.gitea.io/gitea/modules/setting" |
||||
"code.gitea.io/gitea/modules/util" |
||||
packages_service "code.gitea.io/gitea/services/packages" |
||||
|
||||
"github.com/keybase/go-crypto/openpgp" |
||||
"github.com/keybase/go-crypto/openpgp/armor" |
||||
"github.com/keybase/go-crypto/openpgp/packet" |
||||
) |
||||
|
||||
// GetOrCreateRepositoryVersion gets or creates the internal repository package
|
||||
// The RPM registry needs multiple metadata files which are stored in this package.
|
||||
func GetOrCreateRepositoryVersion(ownerID int64) (*packages_model.PackageVersion, error) { |
||||
return packages_service.GetOrCreateInternalPackageVersion(ownerID, packages_model.TypeRpm, rpm_module.RepositoryPackage, rpm_module.RepositoryVersion) |
||||
} |
||||
|
||||
// GetOrCreateKeyPair gets or creates the PGP keys used to sign repository metadata files
|
||||
func GetOrCreateKeyPair(ownerID int64) (string, string, error) { |
||||
priv, err := user_model.GetSetting(ownerID, rpm_module.SettingKeyPrivate) |
||||
if err != nil && !errors.Is(err, util.ErrNotExist) { |
||||
return "", "", err |
||||
} |
||||
|
||||
pub, err := user_model.GetSetting(ownerID, rpm_module.SettingKeyPublic) |
||||
if err != nil && !errors.Is(err, util.ErrNotExist) { |
||||
return "", "", err |
||||
} |
||||
|
||||
if priv == "" || pub == "" { |
||||
priv, pub, err = generateKeypair() |
||||
if err != nil { |
||||
return "", "", err |
||||
} |
||||
|
||||
if err := user_model.SetUserSetting(ownerID, rpm_module.SettingKeyPrivate, priv); err != nil { |
||||
return "", "", err |
||||
} |
||||
|
||||
if err := user_model.SetUserSetting(ownerID, rpm_module.SettingKeyPublic, pub); err != nil { |
||||
return "", "", err |
||||
} |
||||
} |
||||
|
||||
return priv, pub, nil |
||||
} |
||||
|
||||
func generateKeypair() (string, string, error) { |
||||
e, err := openpgp.NewEntity(setting.AppName, "RPM Registry", "", nil) |
||||
if err != nil { |
||||
return "", "", err |
||||
} |
||||
|
||||
var priv strings.Builder |
||||
var pub strings.Builder |
||||
|
||||
w, err := armor.Encode(&priv, openpgp.PrivateKeyType, nil) |
||||
if err != nil { |
||||
return "", "", err |
||||
} |
||||
if err := e.SerializePrivate(w, nil); err != nil { |
||||
return "", "", err |
||||
} |
||||
w.Close() |
||||
|
||||
w, err = armor.Encode(&pub, openpgp.PublicKeyType, nil) |
||||
if err != nil { |
||||
return "", "", err |
||||
} |
||||
if err := e.Serialize(w); err != nil { |
||||
return "", "", err |
||||
} |
||||
w.Close() |
||||
|
||||
return priv.String(), pub.String(), nil |
||||
} |
||||
|
||||
type repoChecksum struct { |
||||
Value string `xml:",chardata"` |
||||
Type string `xml:"type,attr"` |
||||
} |
||||
|
||||
type repoLocation struct { |
||||
Href string `xml:"href,attr"` |
||||
} |
||||
|
||||
type repoData struct { |
||||
Type string `xml:"type,attr"` |
||||
Checksum repoChecksum `xml:"checksum"` |
||||
OpenChecksum repoChecksum `xml:"open-checksum"` |
||||
Location repoLocation `xml:"location"` |
||||
Timestamp int64 `xml:"timestamp"` |
||||
Size int64 `xml:"size"` |
||||
OpenSize int64 `xml:"open-size"` |
||||
} |
||||
|
||||
type packageData struct { |
||||
Package *packages_model.Package |
||||
Version *packages_model.PackageVersion |
||||
Blob *packages_model.PackageBlob |
||||
VersionMetadata *rpm_module.VersionMetadata |
||||
FileMetadata *rpm_module.FileMetadata |
||||
} |
||||
|
||||
type packageCache = map[*packages_model.PackageFile]*packageData |
||||
|
||||
// BuildSpecificRepositoryFiles builds metadata files for the repository
|
||||
func BuildRepositoryFiles(ctx context.Context, ownerID int64) error { |
||||
pv, err := GetOrCreateRepositoryVersion(ownerID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
pfs, _, err := packages_model.SearchFiles(ctx, &packages_model.PackageFileSearchOptions{ |
||||
OwnerID: ownerID, |
||||
PackageType: packages_model.TypeRpm, |
||||
Query: "%.rpm", |
||||
}) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
// Delete the repository files if there are no packages
|
||||
if len(pfs) == 0 { |
||||
pfs, err := packages_model.GetFilesByVersionID(ctx, pv.ID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
for _, pf := range pfs { |
||||
if err := packages_model.DeleteAllProperties(ctx, packages_model.PropertyTypeFile, pf.ID); err != nil { |
||||
return err |
||||
} |
||||
if err := packages_model.DeleteFileByID(ctx, pf.ID); err != nil { |
||||
return err |
||||
} |
||||
} |
||||
|
||||
return nil |
||||
} |
||||
|
||||
// Cache data needed for all repository files
|
||||
cache := make(packageCache) |
||||
for _, pf := range pfs { |
||||
pv, err := packages_model.GetVersionByID(ctx, pf.VersionID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
p, err := packages_model.GetPackageByID(ctx, pv.PackageID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
pb, err := packages_model.GetBlobByID(ctx, pf.BlobID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
pps, err := packages_model.GetPropertiesByName(ctx, packages_model.PropertyTypeFile, pf.ID, rpm_module.PropertyMetadata) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
pd := &packageData{ |
||||
Package: p, |
||||
Version: pv, |
||||
Blob: pb, |
||||
} |
||||
|
||||
if err := json.Unmarshal([]byte(pv.MetadataJSON), &pd.VersionMetadata); err != nil { |
||||
return err |
||||
} |
||||
if len(pps) > 0 { |
||||
if err := json.Unmarshal([]byte(pps[0].Value), &pd.FileMetadata); err != nil { |
||||
return err |
||||
} |
||||
} |
||||
|
||||
cache[pf] = pd |
||||
} |
||||
|
||||
primary, err := buildPrimary(pv, pfs, cache) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
filelists, err := buildFilelists(pv, pfs, cache) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
other, err := buildOther(pv, pfs, cache) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
return buildRepomd( |
||||
pv, |
||||
ownerID, |
||||
[]*repoData{ |
||||
primary, |
||||
filelists, |
||||
other, |
||||
}, |
||||
) |
||||
} |
||||
|
||||
// https://docs.pulpproject.org/en/2.19/plugins/pulp_rpm/tech-reference/rpm.html#repomd-xml
|
||||
func buildRepomd(pv *packages_model.PackageVersion, ownerID int64, data []*repoData) error { |
||||
type Repomd struct { |
||||
XMLName xml.Name `xml:"repomd"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
XmlnsRpm string `xml:"xmlns:rpm,attr"` |
||||
Data []*repoData `xml:"data"` |
||||
} |
||||
|
||||
var buf bytes.Buffer |
||||
buf.Write([]byte(xml.Header)) |
||||
if err := xml.NewEncoder(&buf).Encode(&Repomd{ |
||||
Xmlns: "http://linux.duke.edu/metadata/repo", |
||||
XmlnsRpm: "http://linux.duke.edu/metadata/rpm", |
||||
Data: data, |
||||
}); err != nil { |
||||
return err |
||||
} |
||||
|
||||
priv, _, err := GetOrCreateKeyPair(ownerID) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
block, err := armor.Decode(strings.NewReader(priv)) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
e, err := openpgp.ReadEntity(packet.NewReader(block.Body)) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
|
||||
repomdAscContent, _ := packages_module.NewHashedBuffer() |
||||
if err := openpgp.ArmoredDetachSign(repomdAscContent, e, bytes.NewReader(buf.Bytes()), nil); err != nil { |
||||
return err |
||||
} |
||||
|
||||
repomdContent, _ := packages_module.CreateHashedBufferFromReader(&buf) |
||||
|
||||
for _, file := range []struct { |
||||
Name string |
||||
Data packages_module.HashedSizeReader |
||||
}{ |
||||
{"repomd.xml", repomdContent}, |
||||
{"repomd.xml.asc", repomdAscContent}, |
||||
} { |
||||
_, err = packages_service.AddFileToPackageVersionInternal( |
||||
pv, |
||||
&packages_service.PackageFileCreationInfo{ |
||||
PackageFileInfo: packages_service.PackageFileInfo{ |
||||
Filename: file.Name, |
||||
}, |
||||
Creator: user_model.NewGhostUser(), |
||||
Data: file.Data, |
||||
IsLead: false, |
||||
OverwriteExisting: true, |
||||
}, |
||||
) |
||||
if err != nil { |
||||
return err |
||||
} |
||||
} |
||||
|
||||
return nil |
||||
} |
||||
|
||||
// https://docs.pulpproject.org/en/2.19/plugins/pulp_rpm/tech-reference/rpm.html#primary-xml
|
||||
func buildPrimary(pv *packages_model.PackageVersion, pfs []*packages_model.PackageFile, c packageCache) (*repoData, error) { |
||||
type Version struct { |
||||
Epoch string `xml:"epoch,attr"` |
||||
Version string `xml:"ver,attr"` |
||||
Release string `xml:"rel,attr"` |
||||
} |
||||
|
||||
type Checksum struct { |
||||
Checksum string `xml:",chardata"` |
||||
Type string `xml:"type,attr"` |
||||
Pkgid string `xml:"pkgid,attr"` |
||||
} |
||||
|
||||
type Times struct { |
||||
File uint64 `xml:"file,attr"` |
||||
Build uint64 `xml:"build,attr"` |
||||
} |
||||
|
||||
type Sizes struct { |
||||
Package int64 `xml:"package,attr"` |
||||
Installed uint64 `xml:"installed,attr"` |
||||
Archive uint64 `xml:"archive,attr"` |
||||
} |
||||
|
||||
type Location struct { |
||||
Href string `xml:"href,attr"` |
||||
} |
||||
|
||||
type EntryList struct { |
||||
Entries []*rpm_module.Entry `xml:"rpm:entry"` |
||||
} |
||||
|
||||
type Format struct { |
||||
License string `xml:"rpm:license"` |
||||
Vendor string `xml:"rpm:vendor"` |
||||
Group string `xml:"rpm:group"` |
||||
Buildhost string `xml:"rpm:buildhost"` |
||||
Sourcerpm string `xml:"rpm:sourcerpm"` |
||||
Provides EntryList `xml:"rpm:provides"` |
||||
Requires EntryList `xml:"rpm:requires"` |
||||
Conflicts EntryList `xml:"rpm:conflicts"` |
||||
Obsoletes EntryList `xml:"rpm:obsoletes"` |
||||
Files []*rpm_module.File `xml:"file"` |
||||
} |
||||
|
||||
type Package struct { |
||||
XMLName xml.Name `xml:"package"` |
||||
Type string `xml:"type,attr"` |
||||
Name string `xml:"name"` |
||||
Architecture string `xml:"arch"` |
||||
Version Version `xml:"version"` |
||||
Checksum Checksum `xml:"checksum"` |
||||
Summary string `xml:"summary"` |
||||
Description string `xml:"description"` |
||||
Packager string `xml:"packager"` |
||||
URL string `xml:"url"` |
||||
Time Times `xml:"time"` |
||||
Size Sizes `xml:"size"` |
||||
Location Location `xml:"location"` |
||||
Format Format `xml:"format"` |
||||
} |
||||
|
||||
type Metadata struct { |
||||
XMLName xml.Name `xml:"metadata"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
XmlnsRpm string `xml:"xmlns:rpm,attr"` |
||||
PackageCount int `xml:"packages,attr"` |
||||
Packages []*Package `xml:"package"` |
||||
} |
||||
|
||||
packages := make([]*Package, 0, len(pfs)) |
||||
for _, pf := range pfs { |
||||
pd := c[pf] |
||||
|
||||
files := make([]*rpm_module.File, 0, 3) |
||||
for _, f := range pd.FileMetadata.Files { |
||||
if f.IsExecutable { |
||||
files = append(files, f) |
||||
} |
||||
} |
||||
|
||||
packages = append(packages, &Package{ |
||||
Type: "rpm", |
||||
Name: pd.Package.Name, |
||||
Architecture: pd.FileMetadata.Architecture, |
||||
Version: Version{ |
||||
Epoch: pd.FileMetadata.Epoch, |
||||
Version: pd.Version.Version, |
||||
Release: pd.FileMetadata.Release, |
||||
}, |
||||
Checksum: Checksum{ |
||||
Type: "sha256", |
||||
Checksum: pd.Blob.HashSHA256, |
||||
Pkgid: "YES", |
||||
}, |
||||
Summary: pd.VersionMetadata.Summary, |
||||
Description: pd.VersionMetadata.Description, |
||||
Packager: pd.FileMetadata.Packager, |
||||
URL: pd.VersionMetadata.ProjectURL, |
||||
Time: Times{ |
||||
File: pd.FileMetadata.FileTime, |
||||
Build: pd.FileMetadata.BuildTime, |
||||
}, |
||||
Size: Sizes{ |
||||
Package: pd.Blob.Size, |
||||
Installed: pd.FileMetadata.InstalledSize, |
||||
Archive: pd.FileMetadata.ArchiveSize, |
||||
}, |
||||
Location: Location{ |
||||
Href: fmt.Sprintf("package/%s/%s/%s", url.PathEscape(pd.Package.Name), url.PathEscape(pd.Version.Version), url.PathEscape(pd.FileMetadata.Architecture)), |
||||
}, |
||||
Format: Format{ |
||||
License: pd.VersionMetadata.License, |
||||
Vendor: pd.FileMetadata.Vendor, |
||||
Group: pd.FileMetadata.Group, |
||||
Buildhost: pd.FileMetadata.BuildHost, |
||||
Sourcerpm: pd.FileMetadata.SourceRpm, |
||||
Provides: EntryList{ |
||||
Entries: pd.FileMetadata.Provides, |
||||
}, |
||||
Requires: EntryList{ |
||||
Entries: pd.FileMetadata.Requires, |
||||
}, |
||||
Conflicts: EntryList{ |
||||
Entries: pd.FileMetadata.Conflicts, |
||||
}, |
||||
Obsoletes: EntryList{ |
||||
Entries: pd.FileMetadata.Obsoletes, |
||||
}, |
||||
Files: files, |
||||
}, |
||||
}) |
||||
} |
||||
|
||||
return addDataAsFileToRepo(pv, "primary", &Metadata{ |
||||
Xmlns: "http://linux.duke.edu/metadata/common", |
||||
XmlnsRpm: "http://linux.duke.edu/metadata/rpm", |
||||
PackageCount: len(pfs), |
||||
Packages: packages, |
||||
}) |
||||
} |
||||
|
||||
// https://docs.pulpproject.org/en/2.19/plugins/pulp_rpm/tech-reference/rpm.html#filelists-xml
|
||||
func buildFilelists(pv *packages_model.PackageVersion, pfs []*packages_model.PackageFile, c packageCache) (*repoData, error) { //nolint:dupl
|
||||
type Version struct { |
||||
Epoch string `xml:"epoch,attr"` |
||||
Version string `xml:"ver,attr"` |
||||
Release string `xml:"rel,attr"` |
||||
} |
||||
|
||||
type Package struct { |
||||
Pkgid string `xml:"pkgid,attr"` |
||||
Name string `xml:"name,attr"` |
||||
Architecture string `xml:"arch,attr"` |
||||
Version Version `xml:"version"` |
||||
Files []*rpm_module.File `xml:"file"` |
||||
} |
||||
|
||||
type Filelists struct { |
||||
XMLName xml.Name `xml:"filelists"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
PackageCount int `xml:"packages,attr"` |
||||
Packages []*Package `xml:"package"` |
||||
} |
||||
|
||||
packages := make([]*Package, 0, len(pfs)) |
||||
for _, pf := range pfs { |
||||
pd := c[pf] |
||||
|
||||
packages = append(packages, &Package{ |
||||
Pkgid: pd.Blob.HashSHA256, |
||||
Name: pd.Package.Name, |
||||
Architecture: pd.FileMetadata.Architecture, |
||||
Version: Version{ |
||||
Epoch: pd.FileMetadata.Epoch, |
||||
Version: pd.Version.Version, |
||||
Release: pd.FileMetadata.Release, |
||||
}, |
||||
Files: pd.FileMetadata.Files, |
||||
}) |
||||
} |
||||
|
||||
return addDataAsFileToRepo(pv, "filelists", &Filelists{ |
||||
Xmlns: "http://linux.duke.edu/metadata/other", |
||||
PackageCount: len(pfs), |
||||
Packages: packages, |
||||
}) |
||||
} |
||||
|
||||
// https://docs.pulpproject.org/en/2.19/plugins/pulp_rpm/tech-reference/rpm.html#other-xml
|
||||
func buildOther(pv *packages_model.PackageVersion, pfs []*packages_model.PackageFile, c packageCache) (*repoData, error) { //nolint:dupl
|
||||
type Version struct { |
||||
Epoch string `xml:"epoch,attr"` |
||||
Version string `xml:"ver,attr"` |
||||
Release string `xml:"rel,attr"` |
||||
} |
||||
|
||||
type Package struct { |
||||
Pkgid string `xml:"pkgid,attr"` |
||||
Name string `xml:"name,attr"` |
||||
Architecture string `xml:"arch,attr"` |
||||
Version Version `xml:"version"` |
||||
Changelogs []*rpm_module.Changelog `xml:"changelog"` |
||||
} |
||||
|
||||
type Otherdata struct { |
||||
XMLName xml.Name `xml:"otherdata"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
PackageCount int `xml:"packages,attr"` |
||||
Packages []*Package `xml:"package"` |
||||
} |
||||
|
||||
packages := make([]*Package, 0, len(pfs)) |
||||
for _, pf := range pfs { |
||||
pd := c[pf] |
||||
|
||||
packages = append(packages, &Package{ |
||||
Pkgid: pd.Blob.HashSHA256, |
||||
Name: pd.Package.Name, |
||||
Architecture: pd.FileMetadata.Architecture, |
||||
Version: Version{ |
||||
Epoch: pd.FileMetadata.Epoch, |
||||
Version: pd.Version.Version, |
||||
Release: pd.FileMetadata.Release, |
||||
}, |
||||
Changelogs: pd.FileMetadata.Changelogs, |
||||
}) |
||||
} |
||||
|
||||
return addDataAsFileToRepo(pv, "other", &Otherdata{ |
||||
Xmlns: "http://linux.duke.edu/metadata/other", |
||||
PackageCount: len(pfs), |
||||
Packages: packages, |
||||
}) |
||||
} |
||||
|
||||
// writtenCounter counts all written bytes
|
||||
type writtenCounter struct { |
||||
written int64 |
||||
} |
||||
|
||||
func (wc *writtenCounter) Write(buf []byte) (int, error) { |
||||
n := len(buf) |
||||
|
||||
wc.written += int64(n) |
||||
|
||||
return n, nil |
||||
} |
||||
|
||||
func (wc *writtenCounter) Written() int64 { |
||||
return wc.written |
||||
} |
||||
|
||||
func addDataAsFileToRepo(pv *packages_model.PackageVersion, filetype string, obj any) (*repoData, error) { |
||||
content, _ := packages_module.NewHashedBuffer() |
||||
gzw := gzip.NewWriter(content) |
||||
wc := &writtenCounter{} |
||||
h := sha256.New() |
||||
|
||||
w := io.MultiWriter(gzw, wc, h) |
||||
_, _ = w.Write([]byte(xml.Header)) |
||||
|
||||
if err := xml.NewEncoder(w).Encode(obj); err != nil { |
||||
return nil, err |
||||
} |
||||
|
||||
if err := gzw.Close(); err != nil { |
||||
return nil, err |
||||
} |
||||
|
||||
filename := filetype + ".xml.gz" |
||||
|
||||
_, err := packages_service.AddFileToPackageVersionInternal( |
||||
pv, |
||||
&packages_service.PackageFileCreationInfo{ |
||||
PackageFileInfo: packages_service.PackageFileInfo{ |
||||
Filename: filename, |
||||
}, |
||||
Creator: user_model.NewGhostUser(), |
||||
Data: content, |
||||
IsLead: false, |
||||
OverwriteExisting: true, |
||||
}, |
||||
) |
||||
if err != nil { |
||||
return nil, err |
||||
} |
||||
|
||||
_, _, hashSHA256, _ := content.Sums() |
||||
|
||||
return &repoData{ |
||||
Type: filetype, |
||||
Checksum: repoChecksum{ |
||||
Type: "sha256", |
||||
Value: hex.EncodeToString(hashSHA256), |
||||
}, |
||||
OpenChecksum: repoChecksum{ |
||||
Type: "sha256", |
||||
Value: hex.EncodeToString(h.Sum(nil)), |
||||
}, |
||||
Location: repoLocation{ |
||||
Href: "repodata/" + filename, |
||||
}, |
||||
Timestamp: time.Now().Unix(), |
||||
Size: content.Size(), |
||||
OpenSize: wc.Written(), |
||||
}, nil |
||||
} |
||||
@ -0,0 +1,26 @@ |
||||
{{if eq .PackageDescriptor.Package.Type "rpm"}} |
||||
<h4 class="ui top attached header">{{.locale.Tr "packages.installation"}}</h4> |
||||
<div class="ui attached segment"> |
||||
<div class="ui form"> |
||||
<div class="field"> |
||||
<label>{{svg "octicon-terminal"}} {{.locale.Tr "packages.rpm.registry"}}</label> |
||||
<div class="markup"><pre class="code-block"><code>dnf config-manager --add-repo <gitea-origin-url data-url="{{AppSubUrl}}/api/packages/{{$.PackageDescriptor.Owner.Name}}/rpm/{{$.PackageDescriptor.Owner.LowerName}}.repo"></gitea-origin-url></code></pre></div> |
||||
</div> |
||||
<div class="field"> |
||||
<label>{{svg "octicon-terminal"}} {{.locale.Tr "packages.rpm.install"}}</label> |
||||
<div class="markup"> |
||||
<pre class="code-block"><code>dnf install {{$.PackageDescriptor.Package.Name}}</code></pre> |
||||
</div> |
||||
</div> |
||||
<div class="field"> |
||||
<label>{{.locale.Tr "packages.rpm.documentation" "https://docs.gitea.io/en-us/usage/packages/rpm/" | Safe}}</label> |
||||
</div> |
||||
</div> |
||||
</div> |
||||
|
||||
{{if or .PackageDescriptor.Metadata.Summary .PackageDescriptor.Metadata.Description}} |
||||
<h4 class="ui top attached header">{{.locale.Tr "packages.about"}}</h4> |
||||
{{if .PackageDescriptor.Metadata.Summary}}<div class="ui attached segment">{{.PackageDescriptor.Metadata.Summary}}</div>{{end}} |
||||
{{if .PackageDescriptor.Metadata.Description}}<div class="ui attached segment">{{.PackageDescriptor.Metadata.Description}}</div>{{end}} |
||||
{{end}} |
||||
{{end}} |
||||
@ -0,0 +1,4 @@ |
||||
{{if eq .PackageDescriptor.Package.Type "rpm"}} |
||||
{{if .PackageDescriptor.Metadata.ProjectURL}}<div class="item">{{svg "octicon-link-external" 16 "gt-mr-3"}} <a href="{{.PackageDescriptor.Metadata.ProjectURL}}" target="_blank" rel="noopener noreferrer me">{{.locale.Tr "packages.details.project_site"}}</a></div>{{end}} |
||||
{{if .PackageDescriptor.Metadata.License}}<div class="item" title="{{.locale.Tr "packages.details.license"}}">{{svg "octicon-law" 16 "gt-mr-3"}} {{.PackageDescriptor.Metadata.License}}</div>{{end}} |
||||
{{end}} |
||||
@ -0,0 +1,413 @@ |
||||
// Copyright 2023 The Gitea Authors. All rights reserved.
|
||||
// SPDX-License-Identifier: MIT
|
||||
|
||||
package integration |
||||
|
||||
import ( |
||||
"bytes" |
||||
"compress/gzip" |
||||
"encoding/base64" |
||||
"encoding/xml" |
||||
"fmt" |
||||
"io" |
||||
"net/http" |
||||
"net/http/httptest" |
||||
"testing" |
||||
|
||||
"code.gitea.io/gitea/models/db" |
||||
"code.gitea.io/gitea/models/packages" |
||||
"code.gitea.io/gitea/models/unittest" |
||||
user_model "code.gitea.io/gitea/models/user" |
||||
rpm_module "code.gitea.io/gitea/modules/packages/rpm" |
||||
"code.gitea.io/gitea/modules/setting" |
||||
"code.gitea.io/gitea/tests" |
||||
|
||||
"github.com/stretchr/testify/assert" |
||||
) |
||||
|
||||
func TestPackageRpm(t *testing.T) { |
||||
defer tests.PrepareTestEnv(t)() |
||||
|
||||
packageName := "gitea-test" |
||||
packageVersion := "1.0.2-1" |
||||
packageArchitecture := "x86_64" |
||||
|
||||
user := unittest.AssertExistsAndLoadBean(t, &user_model.User{ID: 2}) |
||||
|
||||
base64RpmPackageContent := `H4sICFayB2QCAGdpdGVhLXRlc3QtMS4wLjItMS14ODZfNjQucnBtAO2YV4gTQRjHJzl7wbNhhxVF |
||||
VNwk2zd2PdvZ9Sxnd3Z3NllNsmF3o6congVFsWFHRWwIImIXfRER0QcRfPBJEXvvBQvWSfZTT0VQ |
||||
8TF/MuU33zcz3+zOJGEe73lyuQBRBWKWRzDrEddjuVAkxLMc+lsFUOWfm5bvvReAalWECg/TsivU |
||||
dyKa0U61aVnl6wj0Uxe4nc8F92hZiaYE8CO/P0r7/Quegr0c7M/AvoCaGZEIWNGUqMHrhhGROIUT |
||||
Zc7gOAOraoQzCNZ0WdU0HpEI5jiB4zlek3gT85wqCBomhomxoGCs8wImWMImbxqKgXVNUKKaqShR |
||||
STKVKK9glFUNcf2g+/t27xs16v5x/eyOKftVGlIhyiuvvPLKK6+88sorr7zyyiuvvPKCO5HPnz+v |
||||
pGVhhXsTsFVeSstuWR9anwU+Bk3Vch5wTwL3JkHg+8C1gR8A169wj1KdpobAj4HbAT+Be5VewE+h |
||||
fz/g52AvBX4N9vHAb4AnA7+F8ePAH8BuA38ELgf+BLzQ50oIeBlw0OdAOXAlP57AGuCsbwGtbgCu |
||||
DrwRuAb4bwau6T/PwFbgWsDXgWuD/y3gOmC/B1wI/Bi4AcT3Arih3z9YCNzI9w9m/YKUG4Nd9N9z |
||||
pSZgHwrcFPgccFt//OADGE+F/q+Ao+D/FrijzwV1gbv4/QvaAHcFDgF3B5aB+wB3Be7rz1dQCtwP
|
||||
eDxwMcw3GbgU7AasdwzYE8DjwT4L/CeAvRx4IvBCYA3iWQds+FzpDjABfghsAj8BTgA/A/b8+StX |
||||
A84A1wKe5s9fuRB4JpzHZv55rL8a/Dv49vpn/PErR4BvQX8Z+Db4l2W5CH2/f0W5+1fEoeFDBzFp |
||||
rE/FMcK4mWQSOzN+aDOIqztW2rPsFKIyqh7sQERR42RVMSKihnzVHlQ8Ag0YLBYNEIajkhmuR5Io |
||||
7nlpt2M4nJs0ZNkoYaUyZahMlSfJImr1n1WjFVNCPCaTZgYNGdGL8YN2mX8WHfA/C7ViHJK0pxHG |
||||
SrkeTiSI4T+7ubf85yrzRCQRQ5EVxVAjvIBVRY/KRFAVReIkhfARSddNSceayQkGliIKb0q8RAxJ |
||||
5QWNVxHIsW3Pz369bw+5jh5y0klE9Znqm0dF57b0HbGy2A5lVUBTZZrqZjdUjYoprFmpsBtHP5d0 |
||||
+ISltS2yk2mHuC4x+lgJMhgnidvuqy3b0suK0bm+tw3FMxI2zjm7/fA0MtQhplX2s7nYLZ2ZC0yg |
||||
CxJZDokhORTJlrlcCvG5OieGBERlVCs7CfuS6WzQ/T2j+9f92BWxTFEcp2IkYccYGp2LYySEfreq |
||||
irue4WRF5XkpKovw2wgpq2rZBI8bQZkzxEkiYaNwxnXCCVvHidzIiB3CM2yMYdNWmjDsaLovaE4c |
||||
x3a6mLaTxB7rEj3jWN4M2p7uwPaa1GfI8BHFfcZMKhkycnhR7y781/a+A4t7FpWWTupRUtKbegwZ |
||||
XMKwJinTSe70uhRcj55qNu3YHtE922Fdz7FTMTq9Q3TbMdiYrrPudMvT44S6u2miu138eC0tTN9D |
||||
2CFGHHtQsHHsGCRFDFbXuT9wx6mUTZfseydlkWZeJkW6xOgYjqXT+LA7I6XHaUx2xmUzqelWymA9 |
||||
rCXI9+D1BHbjsITssqhBNysw0tOWjcpmIh6+aViYPfftw8ZSGfRVPUqKiosZj5R5qGmk/8AjjRbZ |
||||
d8b3vvngdPHx3HvMeCarIk7VVSwbgoZVkceEVyOmyUmGxBGNYDVKSFSOGlIkGqWnUZFkiY/wsmhK |
||||
Mu0UFYgZ/bYnuvn/vz4wtCz8qMwsHUvP0PX3tbYFUctAPdrY6tiiDtcCddDECahx7SuVNP5dpmb5 |
||||
9tMDyaXb7OAlk5acuPn57ss9mw6Wym0m1Fq2cej7tUt2LL4/b8enXU2fndk+fvv57ndnt55/cQob |
||||
7tpp/pEjDS7cGPZ6BY430+7danDq6f42Nw49b9F7zp6BiKpJb9s5P0AYN2+L159cnrur636rx+v1 |
||||
7ae1K28QbMMcqI8CqwIrgwg9nTOp8Oj9q81plUY7ZuwXN8Vvs8wbAAA=` |
||||
rpmPackageContent, err := base64.StdEncoding.DecodeString(base64RpmPackageContent) |
||||
assert.NoError(t, err) |
||||
|
||||
zr, err := gzip.NewReader(bytes.NewReader(rpmPackageContent)) |
||||
assert.NoError(t, err) |
||||
|
||||
content, err := io.ReadAll(zr) |
||||
assert.NoError(t, err) |
||||
|
||||
rootURL := fmt.Sprintf("/api/packages/%s/rpm", user.Name) |
||||
|
||||
t.Run("RepositoryConfig", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req := NewRequest(t, "GET", rootURL+".repo") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
expected := fmt.Sprintf(`[gitea-%s] |
||||
name=%s - %s |
||||
baseurl=%sapi/packages/%s/rpm |
||||
enabled=1 |
||||
gpgcheck=1 |
||||
gpgkey=%sapi/packages/%s/rpm/repository.key`, user.Name, user.Name, setting.AppName, setting.AppURL, user.Name, setting.AppURL, user.Name) |
||||
|
||||
assert.Equal(t, expected, resp.Body.String()) |
||||
}) |
||||
|
||||
t.Run("RepositoryKey", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req := NewRequest(t, "GET", rootURL+"/repository.key") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
assert.Equal(t, "application/pgp-keys", resp.Header().Get("Content-Type")) |
||||
assert.Contains(t, resp.Body.String(), "-----BEGIN PGP PUBLIC KEY BLOCK-----") |
||||
}) |
||||
|
||||
t.Run("Upload", func(t *testing.T) { |
||||
url := rootURL + "/upload" |
||||
|
||||
req := NewRequestWithBody(t, "PUT", url, bytes.NewReader(content)) |
||||
MakeRequest(t, req, http.StatusUnauthorized) |
||||
|
||||
req = NewRequestWithBody(t, "PUT", url, bytes.NewReader(content)) |
||||
req = AddBasicAuthHeader(req, user.Name) |
||||
MakeRequest(t, req, http.StatusCreated) |
||||
|
||||
pvs, err := packages.GetVersionsByPackageType(db.DefaultContext, user.ID, packages.TypeRpm) |
||||
assert.NoError(t, err) |
||||
assert.Len(t, pvs, 1) |
||||
|
||||
pd, err := packages.GetPackageDescriptor(db.DefaultContext, pvs[0]) |
||||
assert.NoError(t, err) |
||||
assert.Nil(t, pd.SemVer) |
||||
assert.IsType(t, &rpm_module.VersionMetadata{}, pd.Metadata) |
||||
assert.Equal(t, packageName, pd.Package.Name) |
||||
assert.Equal(t, packageVersion, pd.Version.Version) |
||||
|
||||
pfs, err := packages.GetFilesByVersionID(db.DefaultContext, pvs[0].ID) |
||||
assert.NoError(t, err) |
||||
assert.Len(t, pfs, 1) |
||||
assert.Equal(t, fmt.Sprintf("%s-%s.%s.rpm", packageName, packageVersion, packageArchitecture), pfs[0].Name) |
||||
assert.True(t, pfs[0].IsLead) |
||||
|
||||
pb, err := packages.GetBlobByID(db.DefaultContext, pfs[0].BlobID) |
||||
assert.NoError(t, err) |
||||
assert.Equal(t, int64(len(content)), pb.Size) |
||||
|
||||
req = NewRequestWithBody(t, "PUT", url, bytes.NewReader(content)) |
||||
req = AddBasicAuthHeader(req, user.Name) |
||||
MakeRequest(t, req, http.StatusConflict) |
||||
}) |
||||
|
||||
t.Run("Download", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req := NewRequest(t, "GET", fmt.Sprintf("%s/package/%s/%s/%s", rootURL, packageName, packageVersion, packageArchitecture)) |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
assert.Equal(t, content, resp.Body.Bytes()) |
||||
}) |
||||
|
||||
t.Run("Repository", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
url := rootURL + "/repodata" |
||||
|
||||
req := NewRequest(t, "GET", url+"/dummy.xml") |
||||
MakeRequest(t, req, http.StatusNotFound) |
||||
|
||||
t.Run("repomd.xml", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req = NewRequest(t, "GET", url+"/repomd.xml") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
type Repomd struct { |
||||
XMLName xml.Name `xml:"repomd"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
XmlnsRpm string `xml:"xmlns:rpm,attr"` |
||||
Data []struct { |
||||
Type string `xml:"type,attr"` |
||||
Checksum struct { |
||||
Value string `xml:",chardata"` |
||||
Type string `xml:"type,attr"` |
||||
} `xml:"checksum"` |
||||
OpenChecksum struct { |
||||
Value string `xml:",chardata"` |
||||
Type string `xml:"type,attr"` |
||||
} `xml:"open-checksum"` |
||||
Location struct { |
||||
Href string `xml:"href,attr"` |
||||
} `xml:"location"` |
||||
Timestamp int64 `xml:"timestamp"` |
||||
Size int64 `xml:"size"` |
||||
OpenSize int64 `xml:"open-size"` |
||||
} `xml:"data"` |
||||
} |
||||
|
||||
var result Repomd |
||||
decodeXML(t, resp, &result) |
||||
|
||||
assert.Len(t, result.Data, 3) |
||||
for _, d := range result.Data { |
||||
assert.Equal(t, "sha256", d.Checksum.Type) |
||||
assert.NotEmpty(t, d.Checksum.Value) |
||||
assert.Equal(t, "sha256", d.OpenChecksum.Type) |
||||
assert.NotEmpty(t, d.OpenChecksum.Value) |
||||
assert.NotEqual(t, d.Checksum.Value, d.OpenChecksum.Value) |
||||
assert.Greater(t, d.OpenSize, d.Size) |
||||
|
||||
switch d.Type { |
||||
case "primary": |
||||
assert.EqualValues(t, 718, d.Size) |
||||
assert.EqualValues(t, 1731, d.OpenSize) |
||||
assert.Equal(t, "repodata/primary.xml.gz", d.Location.Href) |
||||
case "filelists": |
||||
assert.EqualValues(t, 258, d.Size) |
||||
assert.EqualValues(t, 328, d.OpenSize) |
||||
assert.Equal(t, "repodata/filelists.xml.gz", d.Location.Href) |
||||
case "other": |
||||
assert.EqualValues(t, 308, d.Size) |
||||
assert.EqualValues(t, 396, d.OpenSize) |
||||
assert.Equal(t, "repodata/other.xml.gz", d.Location.Href) |
||||
} |
||||
} |
||||
}) |
||||
|
||||
t.Run("repomd.xml.asc", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req = NewRequest(t, "GET", url+"/repomd.xml.asc") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
assert.Contains(t, resp.Body.String(), "-----BEGIN PGP SIGNATURE-----") |
||||
}) |
||||
|
||||
decodeGzipXML := func(t testing.TB, resp *httptest.ResponseRecorder, v interface{}) { |
||||
t.Helper() |
||||
|
||||
zr, err := gzip.NewReader(resp.Body) |
||||
assert.NoError(t, err) |
||||
|
||||
assert.NoError(t, xml.NewDecoder(zr).Decode(v)) |
||||
} |
||||
|
||||
t.Run("primary.xml.gz", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req = NewRequest(t, "GET", url+"/primary.xml.gz") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
type EntryList struct { |
||||
Entries []*rpm_module.Entry `xml:"entry"` |
||||
} |
||||
|
||||
type Metadata struct { |
||||
XMLName xml.Name `xml:"metadata"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
XmlnsRpm string `xml:"xmlns:rpm,attr"` |
||||
PackageCount int `xml:"packages,attr"` |
||||
Packages []struct { |
||||
XMLName xml.Name `xml:"package"` |
||||
Type string `xml:"type,attr"` |
||||
Name string `xml:"name"` |
||||
Architecture string `xml:"arch"` |
||||
Version struct { |
||||
Epoch string `xml:"epoch,attr"` |
||||
Version string `xml:"ver,attr"` |
||||
Release string `xml:"rel,attr"` |
||||
} `xml:"version"` |
||||
Checksum struct { |
||||
Checksum string `xml:",chardata"` |
||||
Type string `xml:"type,attr"` |
||||
Pkgid string `xml:"pkgid,attr"` |
||||
} `xml:"checksum"` |
||||
Summary string `xml:"summary"` |
||||
Description string `xml:"description"` |
||||
Packager string `xml:"packager"` |
||||
URL string `xml:"url"` |
||||
Time struct { |
||||
File uint64 `xml:"file,attr"` |
||||
Build uint64 `xml:"build,attr"` |
||||
} `xml:"time"` |
||||
Size struct { |
||||
Package int64 `xml:"package,attr"` |
||||
Installed uint64 `xml:"installed,attr"` |
||||
Archive uint64 `xml:"archive,attr"` |
||||
} `xml:"size"` |
||||
Location struct { |
||||
Href string `xml:"href,attr"` |
||||
} `xml:"location"` |
||||
Format struct { |
||||
License string `xml:"license"` |
||||
Vendor string `xml:"vendor"` |
||||
Group string `xml:"group"` |
||||
Buildhost string `xml:"buildhost"` |
||||
Sourcerpm string `xml:"sourcerpm"` |
||||
Provides EntryList `xml:"provides"` |
||||
Requires EntryList `xml:"requires"` |
||||
Conflicts EntryList `xml:"conflicts"` |
||||
Obsoletes EntryList `xml:"obsoletes"` |
||||
Files []*rpm_module.File `xml:"file"` |
||||
} `xml:"format"` |
||||
} `xml:"package"` |
||||
} |
||||
|
||||
var result Metadata |
||||
decodeGzipXML(t, resp, &result) |
||||
|
||||
assert.EqualValues(t, 1, result.PackageCount) |
||||
assert.Len(t, result.Packages, 1) |
||||
p := result.Packages[0] |
||||
assert.Equal(t, "rpm", p.Type) |
||||
assert.Equal(t, packageName, p.Name) |
||||
assert.Equal(t, packageArchitecture, p.Architecture) |
||||
assert.Equal(t, "YES", p.Checksum.Pkgid) |
||||
assert.Equal(t, "sha256", p.Checksum.Type) |
||||
assert.Equal(t, "f1d5d2ffcbe4a7568e98b864f40d923ecca084e9b9bcd5977ed6521c46d3fa4c", p.Checksum.Checksum) |
||||
assert.Equal(t, "https://gitea.io", p.URL) |
||||
assert.EqualValues(t, len(content), p.Size.Package) |
||||
assert.EqualValues(t, 13, p.Size.Installed) |
||||
assert.EqualValues(t, 272, p.Size.Archive) |
||||
assert.Equal(t, fmt.Sprintf("package/%s/%s/%s", packageName, packageVersion, packageArchitecture), p.Location.Href) |
||||
f := p.Format |
||||
assert.Equal(t, "MIT", f.License) |
||||
assert.Len(t, f.Provides.Entries, 2) |
||||
assert.Len(t, f.Requires.Entries, 7) |
||||
assert.Empty(t, f.Conflicts.Entries) |
||||
assert.Empty(t, f.Obsoletes.Entries) |
||||
assert.Len(t, f.Files, 1) |
||||
}) |
||||
|
||||
t.Run("filelists.xml.gz", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req = NewRequest(t, "GET", url+"/filelists.xml.gz") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
type Filelists struct { |
||||
XMLName xml.Name `xml:"filelists"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
PackageCount int `xml:"packages,attr"` |
||||
Packages []struct { |
||||
Pkgid string `xml:"pkgid,attr"` |
||||
Name string `xml:"name,attr"` |
||||
Architecture string `xml:"arch,attr"` |
||||
Version struct { |
||||
Epoch string `xml:"epoch,attr"` |
||||
Version string `xml:"ver,attr"` |
||||
Release string `xml:"rel,attr"` |
||||
} `xml:"version"` |
||||
Files []*rpm_module.File `xml:"file"` |
||||
} `xml:"package"` |
||||
} |
||||
|
||||
var result Filelists |
||||
decodeGzipXML(t, resp, &result) |
||||
|
||||
assert.EqualValues(t, 1, result.PackageCount) |
||||
assert.Len(t, result.Packages, 1) |
||||
p := result.Packages[0] |
||||
assert.NotEmpty(t, p.Pkgid) |
||||
assert.Equal(t, packageName, p.Name) |
||||
assert.Equal(t, packageArchitecture, p.Architecture) |
||||
assert.Len(t, p.Files, 1) |
||||
f := p.Files[0] |
||||
assert.Equal(t, "/usr/local/bin/hello", f.Path) |
||||
}) |
||||
|
||||
t.Run("other.xml.gz", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req = NewRequest(t, "GET", url+"/other.xml.gz") |
||||
resp := MakeRequest(t, req, http.StatusOK) |
||||
|
||||
type Other struct { |
||||
XMLName xml.Name `xml:"otherdata"` |
||||
Xmlns string `xml:"xmlns,attr"` |
||||
PackageCount int `xml:"packages,attr"` |
||||
Packages []struct { |
||||
Pkgid string `xml:"pkgid,attr"` |
||||
Name string `xml:"name,attr"` |
||||
Architecture string `xml:"arch,attr"` |
||||
Version struct { |
||||
Epoch string `xml:"epoch,attr"` |
||||
Version string `xml:"ver,attr"` |
||||
Release string `xml:"rel,attr"` |
||||
} `xml:"version"` |
||||
Changelogs []*rpm_module.Changelog `xml:"changelog"` |
||||
} `xml:"package"` |
||||
} |
||||
|
||||
var result Other |
||||
decodeGzipXML(t, resp, &result) |
||||
|
||||
assert.EqualValues(t, 1, result.PackageCount) |
||||
assert.Len(t, result.Packages, 1) |
||||
p := result.Packages[0] |
||||
assert.NotEmpty(t, p.Pkgid) |
||||
assert.Equal(t, packageName, p.Name) |
||||
assert.Equal(t, packageArchitecture, p.Architecture) |
||||
assert.Len(t, p.Changelogs, 1) |
||||
c := p.Changelogs[0] |
||||
assert.Equal(t, "KN4CK3R <dummy@gitea.io>", c.Author) |
||||
assert.EqualValues(t, 1678276800, c.Date) |
||||
assert.Equal(t, "- Changelog message.", c.Text) |
||||
}) |
||||
}) |
||||
|
||||
t.Run("Delete", func(t *testing.T) { |
||||
defer tests.PrintCurrentTest(t)() |
||||
|
||||
req := NewRequest(t, "DELETE", fmt.Sprintf("%s/package/%s/%s/%s", rootURL, packageName, packageVersion, packageArchitecture)) |
||||
MakeRequest(t, req, http.StatusUnauthorized) |
||||
|
||||
req = NewRequest(t, "DELETE", fmt.Sprintf("%s/package/%s/%s/%s", rootURL, packageName, packageVersion, packageArchitecture)) |
||||
req = AddBasicAuthHeader(req, user.Name) |
||||
MakeRequest(t, req, http.StatusNoContent) |
||||
|
||||
pvs, err := packages.GetVersionsByPackageType(db.DefaultContext, user.ID, packages.TypeRpm) |
||||
assert.NoError(t, err) |
||||
assert.Empty(t, pvs) |
||||
|
||||
req = NewRequest(t, "DELETE", fmt.Sprintf("%s/package/%s/%s/%s", rootURL, packageName, packageVersion, packageArchitecture)) |
||||
req = AddBasicAuthHeader(req, user.Name) |
||||
MakeRequest(t, req, http.StatusNotFound) |
||||
}) |
||||
} |
||||
|
After Width: | Height: | Size: 2.6 KiB |
Loading…
Reference in new issue